
Smart Port Project for a Large Science and Technology Company
Standardization of Hyperconverged Factory for a Large Automotive Parts Company
Hyperconverged Infrastructure for Core Applications of a Semiconductor Company
Standardization of VSAN in a Large Automotive Manufacturing Plant
Intelligent Information Network Infrastructure Development for a Large Bank Office Building
Endpoint Security Implementation Project for a Manufacturing Plant
Data Security Compliance Transmission Project for a Large Bank
Disaster Recovery Backup Project with Two Locations and Three Centers for an Airline Company
Sustained Core Database Operations Project for the Semiconductor Industry
HPC Infrastructure Development Project for a Global Automotive Parts Supplier
Cross-Border Data Consulting and Remediation for a Multinational Manufacturing Enterpris
Integration and Operation of a Managed Security Platform for a Foreign Investment Fund
Unified Security Operations Platform Development Project for an Internet Financial Institution
Managed Security Operations Service Project for an Internationally Renowned Cosmetics Brand
Managed Security Operations Service Project for a Currency Brokerage Company
Technical Support for Critical Security Defense for a Leading Domestic Securities Service Provider
Penetration Testing Service Project for an Automotive Parts Manufacturing Company
Security Baseline Scanning Service for the Insurance Industry

With the expansion of the company's operations and the increasing workforce, data security has become an increasingly critical aspect of the company's stable development.
A significant volume of sensitive data and customer information is distributed across various departmental office computers, allowing employees to share sensitive documents with internal
and
external personnel through various means such as USB flash drives, thereby heightening the risk of data leakage.
It is essential to implement related products to mitigate these data security risks.
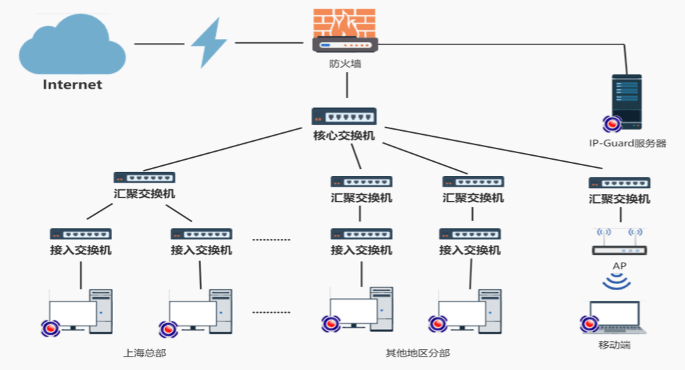
The first stage:
• Conduct a preliminary investigation of the terminal environment and sort key business data.
• Perform demand analysis to confirm the alignment with the appropriate product functionality.
The second stage:
• Implement the deployment of the IPG management platform.
• Conduct small-scale terminal installation, including agent testing and policy tuning.
• Execute a comprehensive push of terminal updates, develop a push plan, and implement it according to the established strategy.
• Track and resolve any arising issues.
The third stage:
• Provide online support and follow-up technical assistance for project delivery.
Address all customer requirements for terminal security and data protection.
Ensuring that the product's reputation can withstand market scrutiny.
A comprehensive data security breach prevention system and associated standards have been established to mitigate the risk of data leakage by users, minimizing disruptions to their normal work and enhancing the convenience of traceability for subsequent data leaks.
Furthermore, the system aims to ensure precise authorization and control over core intellectual property rights and trade secrets, including critical user design data, major business decisions, and strategic development planning.